
Understanding the Man-in-the-Middle Email Scam – How It Works
In a landmark case that highlights the dangers of email fraud, the Gauteng High Court initially held law firm ENS accountable for a client’s loss due to a man-in-the-middle email scam. However, this judgment was later overturned by the Supreme Court of Appeal (SCA).
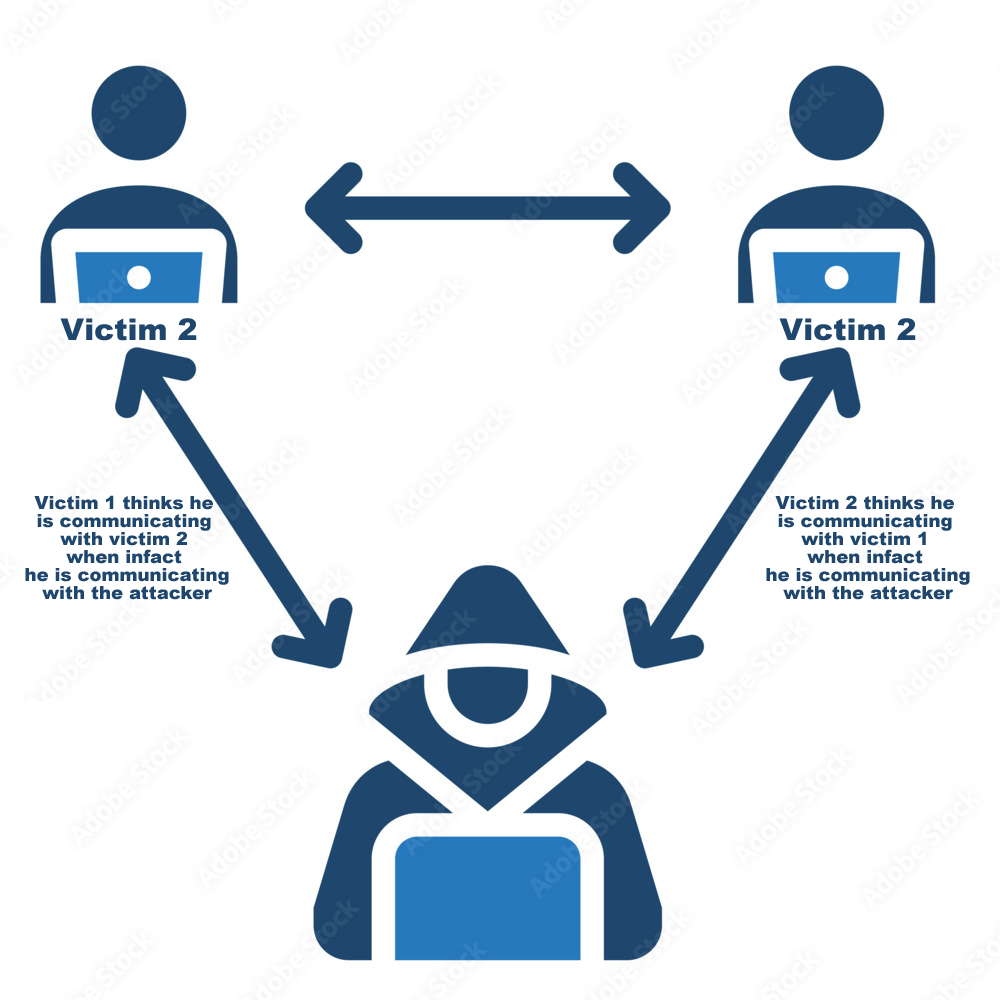
How the Man-in-the-Middle Email Scam Works
The man-in-the-middle (MITM) email scam is a sophisticated form of cyber fraud where attackers intercept and alter communications between two parties without their knowledge. Here’s a step-by-step outline of how the scam typically works:
1. Reconnaissance
- Target Identification: Scammers identify potential targets, often individuals or businesses involved in high-value transactions.
- Email Monitoring: The attackers gain unauthorized access to one or both parties’ email accounts. This can be achieved through phishing, malware, or exploiting weak passwords.
2. Interception
- Email Access: The scammer monitors the email communications between the two parties, looking for details about upcoming financial transactions.
- Waiting for the Right Moment: The attacker waits for an email that contains critical information, such as banking details for a payment.
3. Manipulation
- Email Alteration: The scammer intercepts an email containing bank details and alters the information to redirect the payment to an account they control.
- Spoofing: The altered email is sent to the intended recipient, making it appear as though it is still coming from the legitimate sender. This can involve changing the “reply-to” address or creating a similar-looking email address.
4. Deception
- Fake Communications: The scammer may also send follow-up emails to the victim, posing as the legitimate party to confirm the altered payment details or provide further instructions.
- Avoiding Detection: The attacker ensures that the real sender is unaware of the intercepted and altered communication, often by deleting or hiding the original messages.
5. Execution
- Transaction: The victim, believing the altered email to be legitimate, transfers funds to the scammer’s account.
- Withdrawal: Once the funds are in the scammer’s account, they quickly withdraw or transfer the money to prevent recovery.
6. Aftermath
- Discovery: The fraud is typically discovered when the legitimate party inquires about the payment, and it becomes clear that the funds were sent to the wrong account.
- Investigation: Victims usually contact their banks and law enforcement, but recovering the funds is often difficult as the scammers have already moved the money.
Understanding the Man-in-the-Middle Email Scam: Lessons from Hawarden v ENS
How The Scam Unfolded
The case dates back to 2019 when Julie Hawarden was in the process of purchasing a property, with ENS serving as the conveyancer for the seller. ENS emailed Hawarden their banking details as a PDF attachment, but an unknown hacker intercepted the email, altered the bank details, and sent the fraudulent information to Hawarden. Believing she was making a legitimate transfer, Hawarden sent ZAR 5.5 million to the scammer’s account. By the time the fraud was discovered, the funds had been withdrawn and were unrecoverable.
Initial Judgment: ENS Held Liable
Hawarden sued ENS, claiming the firm failed to use secure communication methods or warn her about the risks of email compromise. The Gauteng High Court sided with Hawarden, stating that ENS, aware of such risks, should have taken more stringent precautions. The court emphasized that as a large, reputable law firm, ENS had a duty of care towards Hawarden, especially given her vulnerability as an elderly, divorced pensioner.
Reversal by the SCA
ENS appealed the decision, and the SCA focused on whether ENS’s actions constituted wrongful omission, causing economic loss. South African law generally does not hold parties liable for losses caused by omissions unless there is a contractual relationship or a specific duty of care. The SCA found that there was no such relationship between Hawarden and ENS.
Hawarden had been previously warned about email fraud by Pam Golding and had multiple opportunities to verify the bank details directly with ENS or through her bank. The SCA concluded that Hawarden had ample means to protect herself and that ENS could not be held responsible for the loss. The appeal was upheld, and ENS was absolved of liability.
Implications and Lessons Learned
Victoria Campos and Micaela Pather of Webber Wentzel highlighted that the SCA judgment underscores the importance of vigilance and secure communication methods in financial transactions. The ruling serves as a reminder that individuals making payments bear significant responsibility for verifying payment details. The case also emphasizes the need for multi-verification processes to prevent such fraud.
While ENS was ultimately not held liable, this case remains a cautionary tale for both businesses and individuals about the critical importance of cybersecurity and due diligence in financial matters.
Preventive Measures – How To Prevent Yourself From Man-in-the-Middle Email Scam
- USETwo-Factor Authentication (2FA): Enabling 2FA on email accounts can significantly reduce the risk of unauthorized access.
- Secure Communication Channels: Use encrypted email services or secure client portals for exchanging sensitive information.
- Verification Procedures: Always verify payment details through a secondary communication channel, such as a phone call, before transferring large sums of money.
- Education and Awareness: Regularly educate employees and clients about the risks of email scams and the importance of cybersecurity practices.
- Monitoring and Alerts: Set up alerts for unusual email activities and monitor financial transactions for any discrepancies.
